Network Security
The protection of the underlying networking infrastructure from unauthorized access, misuse, or theft.

Cybersecurity is a broad field focused on protecting computer systems, networks, and data from unauthorized access, attacks, damage, or theft. It encompasses various technologies, processes, and practices designed to safeguard information and prevent cyber threats.
Key aspects of our cybersecurity includes:
Types of Cybersecurity Consultant

- Threat Data Feeds - APT Intelligence Reporting - Tailored Threat Intelligence Reporting - Financial Threat Intelligence Reporting - Threat Lookup - Cloud Sandbox

- Penetration Testing - Application Security Assessment - Payment Systems Security Assessment - ICS Security Assessment - Transportation Systems Security Assessment - Smart Technologies and IoT Security Assessment

- Comprehensive analysis - Proactive mitigation
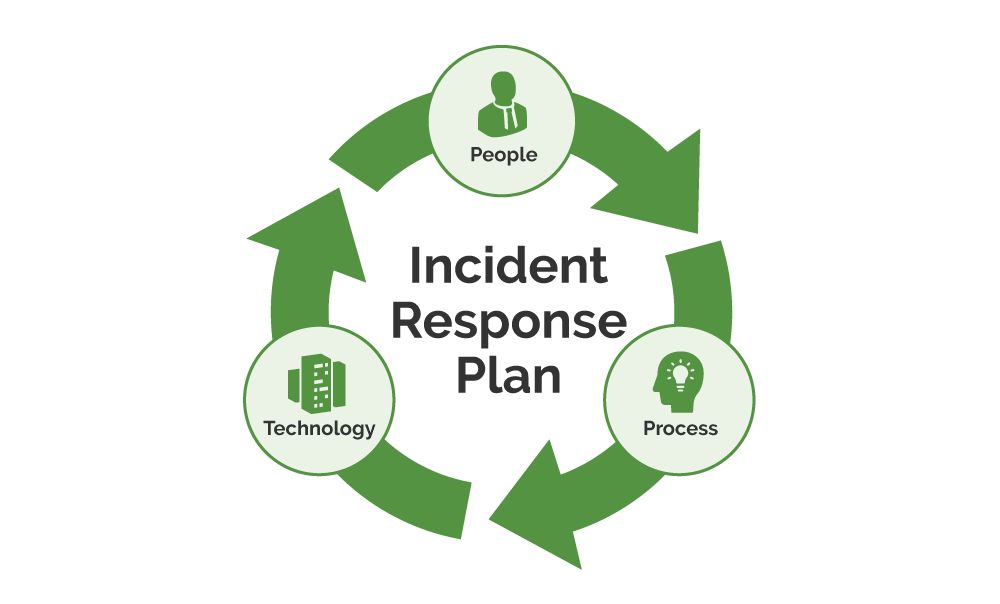
- Digital Forensics - Malware Analysis

- Malware Analysis - Efficient Threat Detection with Yara - Digital Forensics - Incident Response
- Penetration Testing Services - Penetration Testing Costs - Network Penetration Testing - Social Engineering Testing - Blockchain Security Services - Blockchain Penetration Testing Services

- Vulnerability Assessment Services - Network Vulnerability Assessment - Managed Vulnerability Assessment

- Ransomware Business Impact - Cybersecurity - Public Cloud - IT Infrastructure and Networks - Web Application / DevOps - IT Security Audit Services - Cyber Risk Assessment - Remote Work Security Assessment - Medical Device Security Assessment - Blockchain Security Audit - Smart Contract Audit

- Application Security Consulting - Application Security Assessment - Code Review Services

- Cloud Security Consulting - Cloud Security Assessment

- Insider Risk Management - Web Application / Website Protection - Firewall Management - Security Incident Response Management

- Networking basic - Network layer - Network transport - Firewalls - Web applications

